I've figured it out. At first I was confused but now all is clear. You see, we ARE running the…
Could Ransomware’s Rise Be Healthcare’s Downfall?
We look at the evolution of what’s turning out to be the hottest health IT buzzword in 2016 and talk with several cybersecurity experts to gain a technical understanding of the problem.
By @JennHIStalk
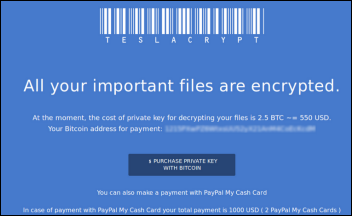
Ransomware. It’s a word that didn’t make most lists of healthcare IT buzzwords to watch in 2016, yet it has become synonymous with industry headlines in the last several weeks. Its mere mention is now perking up the ears of mainstream journalists and evoking a healthy level of fear from hospital CIOs.
Around 10 hospitals in North America (that we know of) have made news due to ransomware attacks. In February, Hollywood Presbyterian Medical Center (CA) became ransomware’s poster child as it went public with its attack and subsequent decision to pay $17,000 in bitcoin to regain control of its hijacked computer systems. MedStar Health (MD) is nipping at the headline heels of HPMC thanks to a late-March attack similar in nature. While the health system has not formally acknowledged the hack as one of the ransomware variety, media reports indicate that its files have indeed been held captive for $18,500.
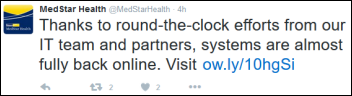
MedStar is still attempting to get back to business as usual with fax machines and paper records. Representatives have been quick to publicly state that care quality — and in most cases, access — have not been compromised, though anonymous hospital employees have indicated otherwise. There’s also the certain mess to clean up once systems are restored and manually recorded information is backloaded and old charges are posted.
As 2016 progresses, hackers and their victims are learning the ransomware ropes. Varieties of attacks are evolving as cybercriminals experiment with new methods of socially engineered phishing campaigns and the levels of extortion their victims will find acceptable. Providers – even smaller physician practices – are reevaluating their IT infrastructure, pointing an especially critical eye at breach protocols already in place and the integrity of their backups.
In addition to these evaluations, the healthcare community is no doubt wondering who will be next and how can these attacks be prevented? Should ransoms be paid? As insidious ransomware spreads, so to do the concerns of providers.
An Evolving Internet Helps Hackers Thrive
As cybersecurity professionals already know, ransomware attacks are nothing new. Late 1980s versions of the business model were spread by floppy disks that locked down files – a highly inefficient method that prevented early attempts at ransomware attacks from becoming widespread. Internet availability helped it creep back in around 2005/2006, and to then take off between 2011 and 2012 as use of the the World Wide Web became more widespread.

“What really changed the game was the first CryptoLocker malware introduced in 2013, which is what we see almost exclusively now for ransomware,” explains Ryan Olson, intelligence director at Palo Alto Networks. “What’s changed since then is an apparent shift in the minds and methods of cybercriminals. They’ve realized that using bitcoin for payment is very profitable, a method much less likely to get them arrested. It’s certainly a far cry from the days of dealing directly with banks and stealing people’s credentials.”
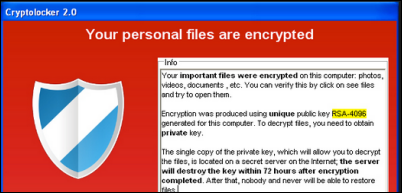
Olson also attributes the rise in ransomware attacks to a corresponding explosion in tools aimed at making the exploits of hackers more effective. “We’re tracking about 30 different types of ransomware right now – from CryptoLocker to Cryptowall to TeslaCrypt – and many of them are being provided to hackers as a service,” Olson says. “If you have a criminal actor who can’t write malware, but who wants to get people’s money through this business model, all they have to do is go out and find a service that will do it for them. All they have to do is distribute the malware and collect the money.”
Thanks, MU (Healthcare Becomes an Easy Target)
It’s not hard to understand why hackers have begun targeting healthcare organizations. The transition away from paper records to digital systems has helped hospitals become a hacker’s sweet spot. “In the past, infecting a bunch of health systems wasn’t very lucrative because trying to monetize stolen healthcare records was pretty challenging,” Olson says. “Most of those computers didn’t have financial information on them. But with ransomware, any system that a hospital needs access to can be a source of monetization. I think that’s something that criminals have realized. Hospitals in particular are a relatively soft target because nearly any system inside their network can be monetized since it is necessary to daily operations and contains sensitive information that hackers can encrypt.”

Patrick Upatham, director of threat intelligence at Digital Guardian, sees hospitals as the latest flavor of the month. “It’s mostly just a numbers game,” he says. “Public services like hospitals ride the double-edged sword of having to publish information about themselves to service their customers, while at the same time providing a map of ingress avenues of attack that can be exploited. The problem stems from when these normal avenues of contact with hospital personnel are leveraged in an attacker’s favor and lead to that one point of weakness that allows them to get their criminal foot in the door.
“This lopsided, or asynchronous, attack model can be easily automated by an attacker to identify and gather contact information for hundreds if not thousands of hospitals,” he adds, “which could then lead to a malicious email sent through an anonymized service. All it would take is one user to click one link, visit one page, or open one document crafted with certain healthcare terminology to infect a machine. Combined with a self-propagating mechanism, a single infection could take its toll on a hospital.”
“Economically speaking,” Upatham adds, “the cost for sending tens of thousands of emails can be recouped 100 times over from a single hospital willing to pay the ransom. Statistically speaking, with the average success rate of a targeted phishing email hovering around 40-50 percent, even at 1 percent, with one hospital out of a 100 falling for it, that can still be good business. These hits are probably just happenstance from the statistical approach of phishing attacks.”
Worming Its Way In
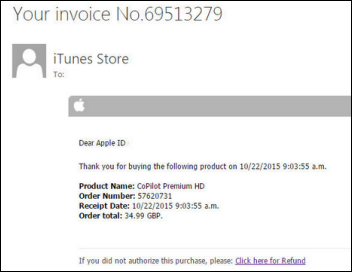
While security firms are monitoring dozens of types of ransomware, most experts agree that the attacks occur in two main ways – phishing emails, as Upatham alluded to above, and exploit kits. “Phishing emails are typically sent indiscriminately to a lot of different people,” Olson explains. “In some cases, they prompt the recipient to open up a file that’s attached to an email. When opened, the file exploits a vulnerability on their computer to infect the system, or tells them to enable macros in Word. We used to have a lot of trouble with macro malware back in the early 2000s, after which Microsoft turned them all off by default so that people weren’t getting infected any more. In 2014, we started seeing attackers use these again in trying to trick people to enable them. The macro is really simple in that it just downloads the malware and puts it on the victim’s computer.” Olson adds that the themes of phishing emails vary. They can include fake package notification messages, fake order reports, and fake travel reports.
While less common than phishing emails, exploit kits are another common method used in ransomware attacks. “Exploit kits are an attacker code that hackers try to inject into Web pages by compromising the Web servers that are hosting them,” he says. “They exploit code by taking advantage of a vulnerability on a victim’s computer to automatically install malware. We call these ‘drive-by downloads’ because they install the malware so quickly and stealthily.”
The Realities of Successful Prevention
When it comes to preventative measures, healthcare systems can’t rest on their IT laurels. Neither can they settle for the advice of the latest “listicle” and its high-level admonitions to educate, back up, and prepare. Enterprise healthcare IT environments are far more nuanced than a 10-bullet-point list and it seems that no amount of investment will successfully overcome human nature’s inclination to click.

“It’s all great advice, but some of it is totally impractical,” says David Finn, health information technology officer at Symantec and recently appointed member of the new HHS Cyber Security Task Force. “Healthcare isn’t going to stop using email. You can’t tell physicians and nurses they can’t get on the Web. There are a couple of steps you have to take. The first thing is look at the battle today – the good guys versus the bad guys. The battleground is really the end point again, so you have to start there with good security on all your end points. It has to be installed, updated, and patched regularly, which is where a lot of organizations fall down.”
“The second step,” Finn continues, “which is almost as important as the first, is user education. Computers don’t click on dangerous links and tablets don’t open emails they’re not supposed to – people do. In Hollywood Presbyterian’s case, for example, every employee at that organization received an email with what appeared to be a legitimate invoice. It’s really hard for people, when they think they’re getting a bill for something, to not open it even though they may not have bought anything.”
Upatham likens the need for user education to good hygiene: “Educating users about possible attack attempts and making sure they practice good online hygiene should go hand in hand with hospital hygiene. If any place of employment should understand the implications of introducing viruses to a healthy system through dangerous means, it should be in a hospital. The same stress and education should be extended to online access.”
Once good online hygiene and end-point security are addressed, providers still must deal with a laundry list of other less sexy but just as important preventative measures. “You do have to have content scanning and filtering under your email systems and on your Internet gateways,” Finn adds. “Attackers frequently use old vulnerabilities to use filter command and control structures to send data out, so you have to have all your servers and all your storage patched and current with your operating systems, and all the utilities that should be on those devices.”
“Then of course you need to have some kind of advanced threat protection looking at intrusion prevention or intrusion detection, because a lot of times malware comes in and lives on your network for extended periods – months and months, even up to a year, while it’s mapping data and networks. It’s probably doing a better job than most of our organizations actually do when it comes to that. You pretty much have to be on the lookout for anomalous activity all the time. And that brings us back to end-point security again so that the worm isn’t working through and propagating itself across the whole network.”
“Last but certainly not least,” says Finn, “and this is the one everyone hollers about, is the need to deploy and maintain a comprehensive backup solution. That includes having protection and anti-malware on the storage itself. If you’re relying on the backup groups, and the backup PC gets infected, you’re shooting yourself in the foot because this new malware is pretty sophisticated. It will look for those backups, find where those backups are going, and then it will encrypt them, too. You need to look at the storage and the storage needs to be completely offline from the typical point of entry for these malware devices.”
Olson believes that the biggest preventative challenge healthcare organizations are running into involves shared storage systems. “When a system gets infected and it’s attached to a shared storage system – a network drive of some kind that’s configured so that any user can write files to it – in those cases, the malware will actually go in and find that network storage drive where everybody is sharing all of their files and encrypt all of them. That’s where the biggest impact occurs. At that point, you’ve gone from a single system that was impacted to suddenly all of the systems that rely on that shared data. Now none of them can access the data, and you have a much bigger problem than you had before. Limiting access to those shared drives is another component of protection against ransomware.”
Ransomware Requires Rethinking Strategy and Budgets
The MedStar attack – the fourth such healthcare breach to occur in just a few weeks – should serve as a wakeup call to healthcare executives across the country, according to Upatham. “Hackers are after the healthcare industry now more than ever,” he notes. “Now that they’ve easily cracked a handful of hospital firms, and many have paid the ransom fees, hackers will continue to attack for additional monetary gain.”
Finn concurs that the time is now for the healthcare C-suite to wake up: “Everyone needs to be rethinking their strategy, and not just around ransomware. We complain about the pace of change in healthcare, but the bad guys are moving way faster than us. They don’t have the constraints of regulations, taxes, and budgets. It’s easier for them to get ahead of us than it is for us to get ahead of them. If there’s one lesson we can take away from all this, and not to kick someone when they’re down, but if you look at Hollywood Presbyterian, they didn’t pay that ransom to get access to computers or to get data back, though that was ostensibly what was happening. They paid the ransom because they couldn’t take care of sick people. That’s a business issue. That’s not an IT issue. Until the CEOs, CFOs, CNOs, and CMOs recognize that this is really a threat to their business and ability to care for patients, I don’t think IT will get the support it needs in terms of staff, budget, tools, and training.”

In terms of budget priorities, Sensato CEO John Gomez suggests making two immediate purchasing decisions. “Invest in the latest backup software available,” he says, “and, beyond that, get someone to do a backup and recovery assessment. Make sure it is holistic and frequent, and make sure you test your ability to recover. If you can’t back up, you will pay your attackers. The second investment is in user education. Every independent software vendor, independent hardware vendor, provider, and payer should be informing their users about what to look for, and that should come from the CEO. Users need to understand that being aware is critical to avoiding attacks.”
Preparing for What Comes Next
As Finn previously mentioned, cybercriminals are always one step ahead of the game, unencumbered by the constraints of law-abiding organizations. Thus, it’s nearly 100-percent guaranteed that ransomware attacks will continue to evolve in an attempt to develop an immunity to healthcare’s defenses.
“I wish I could say that all providers have to do is back up, test, and educate,” says Gomez, “but ransomware is evolving. Last week, the FBI issued a warning about a new strain of ransomware that doesn’t use phishing attacks as the attack vector. Although back up, test, and educate is a short-term fix, the reality is that you either decide cybersecurity is a top three priority for your organization and take aggressive steps to lock things down, or you’re pretty much rolling the dice.”
“The last thing to keep in mind,” he says, “is that ransomware is just the attack du jour. It’s not like attackers will say, ‘Ok, we’ve messed with healthcare enough, now let’s go mess with finance for a while.’ Attacks will evolve and a whack-a-mole approach to cybersecurity is not going to work. You need a holistic, long-term, and aggressive strategy.”
Olson sees the evolving Internet of Things as the perfect conduit to a corresponding evolution of the ransomware business model. “If an attacker is able to compromise some sort of device, even though it’s not a traditional computer, one of the monetization mechanisms they might have for that is to hold it for ransom. That’s something we really haven’t seen before, but I fully expect to see it in the future as these devices come online and attackers start to search for new systems they can infect, take over, and turn into a profit. It would not surprise me if we saw ransomware attacks against medical devices. I hope that’s not the direction that attackers go, simply because they’re preying on the most vulnerable people.”
“We know that medical devices have fallen victim to ransomware,” Gomez confirms. “As best we can tell, the devices were not the target of the attack, but rather fell victim to a form of ransomware that attacks much like a virus, for lack of a better term. The virus spreads and just does its thing across the network. As scary as that is, the bigger issue we will no doubt soon face is the purposeful attack of a medical device. I started the Medical Device Cybersecurity Task Force, an open-source nonprofit, to specifically address the challenges faced by the industry in securing medical devices. We are currently working on compiling 25 short-term steps that a healthcare organization should consider to secure their devices. We are also conducting research in our labs and running several pilots with three different healthcare organizations.”
Best Practices Can Only Come From Learning Experiences
Healthcare, unfortunately, will likely have to suffer through several dozen or more ransomware attacks before providers can definitively say what worked and what didn’t in terms of prevention and remediation. Finn is hopeful that the nascent HHS Cyber Security Task Force will help the healthcare community share recommendations that will ultimately influence federal legislation.
“You know that in healthcare, we’re not only siloed within the four walls of the hospital, but across the industry,” he says. “In terms of new care models and new security models, that is going to have to change. It’s going to take all of us. Whether we’re providers, vendors, or business associates, we’re all going to have to come together and decide what the addressable items need to be. We’re going to have to have some way of knowing what everyone else is doing to prevent their organizations from becoming the next victim. If there’s one thing we do know, it’s that everyone trying to solve security issues by themselves doesn’t work. We’ve all got to come together and drive a consistent message across this industry.”


What a well researched article! Thank you for putting this latest news into perspective with what the industry is facing and what can be done about it.
Ditto – Excellent and important piece of journalism. Thank you.
Well done article, so much better than the usual poorly researched regurgitation we normally see. Hope you carry on this important thread, would like to see you cover the current state of healthcare cybersecurity in the U.S. and compare and contrast to what other countries are doing. IMHO there’s probably 20 or so IDN’s large enough and sophisticated enough to provide for their own defenses, with the vast majority of CAH and smaller community hospitals terribly exposed. The federal government could really make itself useful and start aggressively (emergency basis?) providing resources to provide for some of the measures called for by the experts cited in your article – can we really wait years for the HHS Cyber Security Task Force recommendations and then legislative cycle?.
We have seen small medical practices infected with ransomware as well. This is not just a hospital system issue. Thank you for a very informative piece.
Although medical practices of all sizes have been slow to respond to the security threat, I think that the current round of ransomware will change things.
As the article states, ransomware goes right to the heart of the clinical practice, preventing administration of medicine and treatment of patients. It’s an existential threat and will be responded to as such.
Paying the ransom is expedient at the moment. I expect that too will change as the criminals return again and again. Blackmailers always do. Expect the rate of ransom payments to decline as organizations who don’t already know this, learn it.
Security is going to rocket to the top of the To-Do list in the next year.
Excellent article on this menace to our industry. I am shocked by how easy this can be used as a tool to extort $$ and potentially destroy a system.
Brian Too is correct…this is an existential threat that needs to be dealt with. Prevention is the key; detection and eradication before the ransom event is IMPERATIVE.
Awesome article. My practice just had to pay $1600 in ransomeware for an eClinical Works hack today. Still not back up and running… this is a real issue.