How Providers Are Addressing Ransomware
Providers share their methods for staying one step ahead of healthcare’s latest foe.
By @JennHIStalk
While national headlines related to ransomware attacks on hospitals seem to have abated – for now – the healthcare industry’s interest in the latest cyberattack trend has only intensified. Research related to provider preparedness seems to come out weekly, highlighting what has by now become common knowledge: healthcare has a lot of work to do.
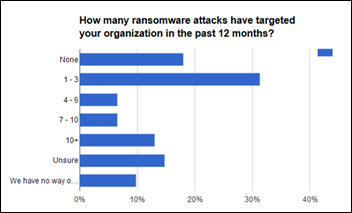
A HIMSS study released in early April found that 75 percent of surveyed hospitals were or could have been hit with a ransomware attack in the last year, with a significant number or respondents saying they aren’t sure or have no way to tell. Statistics like these make IBM’s data on industry-wide breaches in 2015 that much more believable, where the global company’s Cyber Security Intelligence Index found that healthcare was the most-attacked industry in 2015 with over 100 million patient records compromised.

The industry is working to handle what seems like a non-stop assault. HHS has created a Cyber Security Task Force to develop recommendations and best practices that could eventually impact legislation. Intermountain Healthcare (UT) has partnered with the University of Utah to establish a joint security center to help providers keep up with the latest cybersecurity threats, while providers in the trenches seem focused more than ever on assessing their cybersecurity vulnerabilities.
Taking a Proactive Approach


Northwell Health, a New York-based IDN with 21 hospitals and 450 ambulatory sites, has taken a proactive approach to cybersecurity, according to Mark Jarrett, MD, senior vice president, chief quality officer, and associate CMO. (Jarrett also serves on the new HHS task force.) “Recent events have only supported our enterprise-wide efforts to secure our network,” he explains. “We are performing hazard vulnerability assessments on a regular basis. As news becomes public of new events, we adapt our defenses. Maintaining all current security patches on our multiple systems is also key. To prevent ransomware attacks, we are employing all standard intrusion techniques from technical, such as firewalls, to staff education and testing so that they understand social phishing and the risks of non-certified thumb drives. We remain concerned as the sophistication of intruders to introduce malware has been increasing.”


Across the country, Texas Health Resources, a health system with 25 hospitals and 69 outpatient facilities serving the Dallas-Fort Worth area, has taken a similar approach. “In the last couple of years, we started to take aggressive action to defend against threats such as ransomware,” says Luis Saldana, MD, CMIO and medical director for clinical decision support. “This action included targeted reduction of direct user access to certain forms of unstructured data such as DICOM images and PDF files. We also have a robust anti-phishing program to reduce the possibilities of a user receiving or being lured into clicking on potentially malicious email links. We’ve also validated our backup and restoration strategies and have fine-tuned our incident response when we detect a ransomware attack.”
In terms of keeping up with emerging security threats, Saldana adds that Texas Health’s cybersecurity program is designed to continuously evolve and adapt. “We do this through a continuous risk-management philosophy that is linked to operations.”
Size Matters
Northwell and Texas Health are capable of taking such proactive approaches thanks to their internal resources – a luxury that smaller hospitals and physician practices are not typically afforded. “I believe small- to medium-sized health systems of stand-alone hospitals and practices that hadn’t had the opportunity to invest in a robust infrastructure to defend against this kind of threat, or that are unable to attract cybersecurity professional talent might be more vulnerable to the impact of such an attack,” says Saldana. “We are fortunate to have a fairly sophisticated cybersecurity program.”
Jarrett points out that with greater resources comes greater vulnerabilities. “Although our size allows us to have more resources than a small hospital or group of hospitals, it also means that there are many more potential sites for failure of our defenses,” he explains. “With 61,000 employees, the task of maintaining a high level of awareness around social phishing is monumental.”
Culture and Consultants Do, Too
Both Jarrett and Saldana are quick to point out that their organizations see cybersecurity threats like ransomware as more than just a problem for the IT department to solve. “Our organizational culture is really what makes this work,” says Saldana. “Our C-suite is very educated on the issues and very supportive, and the programs have been broad in scope – beyond just IT.”
“The C-suite recognizes this is not just an IT issue,” Jarrett adds. “They have supported IT in its efforts to ensure network security.”
For both organizations, support also comes in the form of outside expertise. Northwell engages third-party consultants to evaluate its cybersecurity and provide an outsider approach to vulnerabilities. Texas Health Resources has multiple partners that perform periodic testing of its internal and external defenses, as well as monitor its cyber defenses. “We have selected these vendors through proof-of-concept testing and self-defined cybersecurity capability needs,” Saldana explains.
Prevention Boils Down to Awareness
Saldana believes that cybersecurity prevention and preparation begins with awareness. “The first step is to acknowledge that you are constantly being targeted by threats,” he explains. “Then, backups, backups, backups. Know your recovery time requirements and build backup restoration capabilities to match those requirements. Ensure you have an effective and tested business continuity plan for scenarios when data might be unavailable.”
Saldana also suggested that providers keep their tools up to date and conduct frequent phishing training and testing to prepare employees. “Have an incident response plan in place and prepare your employees to have a heightened awareness,” he adds. “Carefully manage access and be prepared to respond and practice your plan. And don’t forget to keep up with industry intelligence. It’s important to see and learn from other organizations in many areas and to support other organizations who are targets for these types of threats.”
Learning from Hospital Peers

The Intermountain / University of Utah shared Security Operations Center will play a big part in helping providers share industry intelligence around cybersecurity threats in real time. “It will be an opportunity for partner organizations to share learnings and intellectual property around security,” says Intermountain CIO Marc Probst. “There is also the opportunity to share some technical solutions and security intelligence. For example, the ability to immediately understand threats that other organizations are experiencing and to take action to prevent these at your own organization. To the extent organizations are members of the shared SOC, they could inherit these benefits.”
Probst adds that organizers hope to see the center up and running before the end of this year. “There are many details to work out.” he explains, “It’s possible that the participants could change and/or increase. There’s still a lot of work to do, but we are convinced that this is a good idea and we are actively pursuing it.”
Probst’s words reflect the learning curve the healthcare industry is still experiencing when it comes to cybersecurity and more targeted ransomware attacks. There is still – and will likely always be – a lot of work to do. Culture, collaboration, and vigilance will be key to ensuring that ransomware-related headlines soon become a thing of the past.


Once we settle in to the Epic monopoly for a couple decades, what will the market look like for healthIT?…