Hard agree, and not just because I'm a spreadsheet nerd. Why are we all here? Isn't it in the service…
Weekender 10/15/21

Weekly News Recap
- Intelerad acquires Ambra.
- Healthcare Triangle shares drop after IPO.
- GetWellNetwork renames itself to Get Well.
- A security researcher documents widespread security vulnerabilities in FHIR APIs.
- Best Buy announces its planned acquisition of Current Health.
- Cerner President and CEO David Feinberg, MD, MBA kicks off the virtual Cerner Health Conference with a call to “eliminate the noise in healthcare.”
- SSM Health outsources services, including digital transformation and RCM, to Optum and will send 2,000 employees to the company.
- The VA contracts for a year-long cost review of its Cerner implementation.
Best Reader Comments
The NPfIT attempted to build a system rather than buy one. My pet theory is that this is part of why the NHS failed with NPfIT. Having an existing system to implement automatically puts all sorts of conceptual stakes in the ground. You not only get the What will this system do, you also get the How and the Why laid out for you. Ultimately, this is why purchasing third-party software eclipsed homegrown systems. Well, that and the ability to spread the development costs around. (Brian Too)
I believe this announcement [of the VA’s 12-month Cerner implementation cost review] still requires far more of an explanation than was given. I think an explanation can be given that protects the identities and dignity of VA employees, but also makes it clear that changes are underway. This organization still serves a gigantic public need for a very valued constituency. Our veterans really do deserve a lifetime of strong support from the VA. I want to recognize that there is a lot of good work the VA does in fulfilling that mission. This project sounds like a corner where the VA may not be living its values. (Accountabilibuddy)
UHC is amassing a huge presence in healthcare (data, contracted patient lives, POC resources, etc), where they can use their position to control cost and access, much in the same way people fear digital companies like Google having access to large amounts of healthcare data. Your CIO audience should be concerned about the motives of these vendors, short and long term. They are in it to make money, many times at the expense of patients. (Susanna Stevens)
I don’t want to diminish [Seve] Job’s legacy in tech, because it is truly massive. That said, I think his early death is a good parable for Apple (and others) attempts to break into healthcare technology. Steve Jobs died because he thought he was smarter than oncologists who had studied cancer for years, and appeared to think he was smarter than the healthcare delivery system as a whole. Had Jobs pursued traditional treatment as soon as his cancer was detected, he would very likely be alive. He should be a very real warning to every startup and VC that thinks they are smarter than the people who have actually been doing it for their whole career. (Elizabeth H. H. Holmes)
Watercooler Talk Tidbits

Readers funded the Donors Choose teacher grant request of Ms. R in Oklahoma, who asked for a tripod stand and microphone for conducting virtual classes. She reports, “I am beyond blessed to have people like you continue to believe in the importance in education even during difficult times. Teaching online is difficult as it is, but knowing I have wonderful people like you who are willing to go the extra mile warms my heart and gives me the energy to keep doing the best I can for my students. Thank you once again and may God bless you for your contribution to this wonderful project.”
In England, an NHS nurse is fired for refusing psychiatric help after losing her lawsuit against a hospital that she claimed was secretly hypnotizing her, which she says caused headaches, breathing difficulty, uncontrollable flatulence, and unspecified attacks on her private parts.

Harborview Medical Center (WA) nurse Guy Maddison, RN launches a podcast that interviews hospital workers about the challenges of caring for COVID patients. Maddison is also the bass player for Seattle cult grunge band Mudhoney.
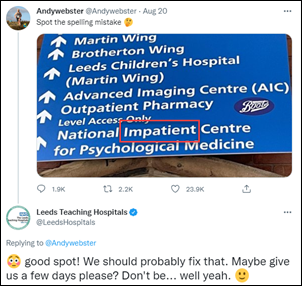
England’s Leeds Teaching Hospitals responds good naturedly to a sign’s spelling error that was called out on Twitter.
In Case You Missed It
- News 10/15/21
- EPtalk by Dr. Jayne 10/14/21
- HIStalk Interviews Shawn DeWane, CEO, TransformativeMed
- News 10/13/21
- Curbside Consult with Dr. Jayne 10/11/21
- Readers Write: Engaging Patients with Social Determinants of Health: Is Your Practice Ready?
- Readers Write: The Next Generation of Intelligent Decision Support
- Readers Write: Why Patient Control of their Own Data is the Key to Health Equity
- Monday Morning Update 10/11/21
Get Involved
Sponsor
Report a news item or rumor (anonymous or not)
Sign up for email updates
Connect on LinkedIn
Contact Mr. H



Re: FHIR API Vulnerabilities.
“EHR security was strong, but third-party data aggregators and mobile apps were full of security holes.” It’s almost like this is exactly what Epic was arguing about the Interoperability Rule. I brought this up MANY times on this blog as the proposed rule moved along:
https://histalk2.com/2020/01/31/weekender-1-31-20/
https://histalk2.com/2020/01/27/epic-lists-its-hhs-interoperability-rule-concerns/
While we’re at it, can we talk about how pretty much all of the interoperability standards for healthcare are not secured? HL7 is not an inherently secure protocol. DICOM is not an inherently secure protocol. I don’t think X12 are inherently secure protocols either. The protocols don’t support any native encryption and have little to no authorization/authentication mechanisms. So our healthcare InfoSec friends basically have two overlapping options: 1) encapsulate these messages in a protocol that is secure; 2) Use network microsegmentation to limit which endpoints on your network are allowed to talk to your databases.
The problem with #1 is that while it’s doable in theory, and there is even an RFC for doing this with X12, I haven’t seen any commercial products or solutions that implement it. Not once in a decade of system administration including EDI networking. Everything we did was just firewall management. If you had access to either machine or the wire you could easily sniff the packets and see the plaintext information flowing. The problem with #2 is that it is manual and mistake-prone. Your security posture is only as good as your firewall upkeep and your awareness of your health databases (you probably have more than you think).
All of this leads me to the conclusion of:
1. Develop a commercially-ready healthcare protocol encapsulation solution that implements TLS + token based authorization
2. Make an open source commit to metasploit and other offensive security tools which includes out of the box HL7/DICOM/X12/FHIR exploit techniques
3. Publish a number of security blogs calling attention to how insecure this is and how there are tools available to exploit it
4. Profit
It would be a much better business idea than a lot of the start ups I see on here. Even though EHRs are reasonably secure for now, HIT is in for even more serious security reckonings if we can’t make future versions of these protocols that do a better job of implementing zero-trust security concepts.
Correct that HL7 v2, DICOM, X12 etc do not have security in the protocols themselves – they are routinely secured by microsegmentation as detailed. I’m not persauded that it’s more mistake prone than the alternatives – and it’s at least easier to test (but does need testing). FHIR is different – it’s built on the the web stack in order to get web level security. But as the report shows, that requires actual commitment to security to get right.
But #2: a commit to metasploit… sounds like a good idea for someone to do
My understanding is that the scope of any given standard is often NOT driven by drop-in usability concerns. Instead, the following tend to dominate scope discussions:
1). The perceived level of support for the standard (more resistance routinely leads to narrower scope);
2). Philosophical considerations of “what” a clinical standard ought to address;
3). The assessed market need for flexibility. Since the issue of flexibility is notoriously difficult to standardize, one go-to response is to externalize all areas requiring flexibility.
Since the subject you’ve raised is security, well security is surely an area requiring flexibility. Thus what do you implement? AES? ECC? What should the key length be? Do we need to worry about quantum decryption attacks? Did the NSA really weaken this or that algorithm, and if so, by how much? Who do you trust and why?
Honestly, security can be one giant argument that never ends.